The PDC Emulator is one of the five Flexible Single Master Operations (FSMO) roles found in an Active Directory (AD) forest. There is only one Domain Controller (DC) in each domain that holds this role. By default, this is the first server that was promoted to a DC in the domain.
The main purpose of the PDC Emulator is to operate as a Primary Domain Controller (PDC) for pre-Windows 2000 clients such as Windows 95, Windows 98, and Windows NT 4.0. At any given time, only one Domain Controller in the domain can hold this role. Most commonly, you may still find some lingering Windows NT 4.0 clients on Active Directory domains. They need the PDC Emulator to authenticate and process password changes.
Another important role that the PDC Emulator handles is maintaining password updates for the domain. All password changes made on other DCs are sent to the PDC Emulator for urgent replication. This type of replication does not adhere to inter-site replication schedules.
In addition, when authentication fails for a user being authenticated by another DC, authentication is retried on the PDC Emulator. If the password was recently changed, but replication has not been fully propagated, the user will be able to authenticate using the PDC Emulator regardless of the site that the user’s computer is a member of.
Another critical role performed by the PDC Emulator is time synchronization for the domain. The PDC Emulator in the root domain is generally configured to sync its local clock with an authoritative NTP server. This NTP server may be located on the internet, such as time.windows.com, or it can be a device on your internal network, such as a GPS atomic clock.
The PDC Emulators in the child domains will synchronize their time with the root PDC Emulator. Domain Controllers in the domain sync with the PDC Emulator in their respective domains. Clients will then sync their clocks with the DCs in their domain. Time Synchronization is critical for the Kerberos protocol to authenticate successfully.
If the PDC Emulator were to fail, you may want to restore this role as soon as possible, especially if you have down-level clients. Your domain won’t stop working at the time of failure, but over a long period of time, you will impact your environment. If you plan on returning the failed server back to service within a few hours, then you may just want to operate without the PDC emulator during that time.
If the outage will be extended, you should seize the role to another DC in the domain. Of course, if you plan on bringing down the PDC emulator for extended maintenance, you should gracefully transfer the role. There are two methods for transferring the PDC Emulator role. You can use the Active Directory Users and Computers snap-in (only if both DCs, source, and target, are operational), or ntdsutil.
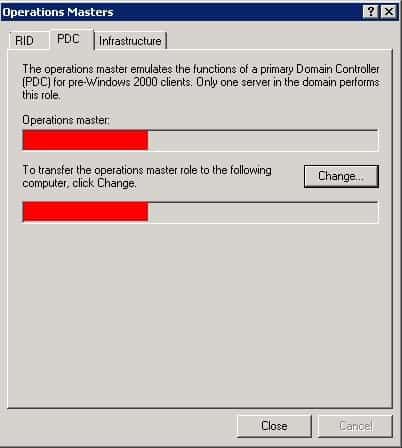
Transferring the PDC Emulator role is quite easy. Using the Active Directory Users and Computers snap-in, connect to the target DC. Then, right click the domain object and click on Operations Masters. Now click on the PDC Emulator tab. In the top box, the current DC holding the role should be displayed. In the lower box, you should see the name of the DC that you wish to transfer the role.
Or, using the ntdsutil.exe command, type roles and hit [enter]. Then type connections and hit [enter]. Next typeconnect to server servername and hit [enter]. Type quit and hit [enter]. The system will bind and continue. Then type transfer pdc and hit [enter]. A confirmation dialog box will be displayed. Click on Yes. The system will provide some feedback in regards to this action.
The process of transferring the PDC Emulator role is complete.